I just landed a nifty new feature for OpenKeychain. It’s simple enough: If you want to communicate privately with someone, you need their key. So, just like when you’re looking for anything else, you type their name or email or whatever into a search box and find it on the Internet.
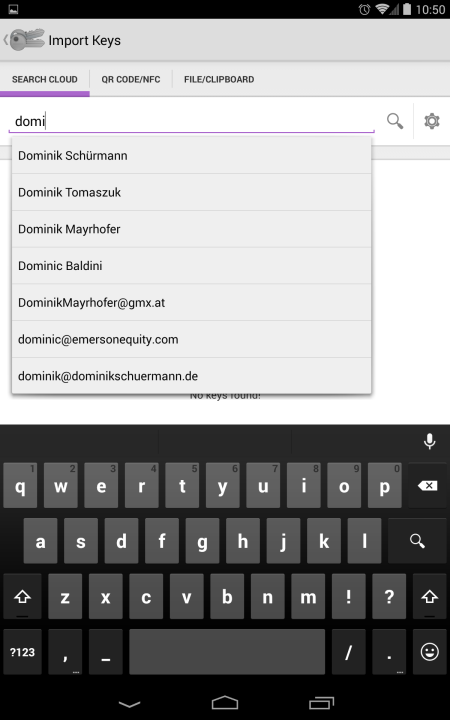
Here’s how it looks · Suppose I want to communicate with Dominik Schürmann; he’s the lead author of OpenKeychain and a good example because of his long hard-to-type name. I start entering it… ¶
Since he’s is in my Android contacts, I can pick him from the drop-down and not type much. Here’s what the search yields:
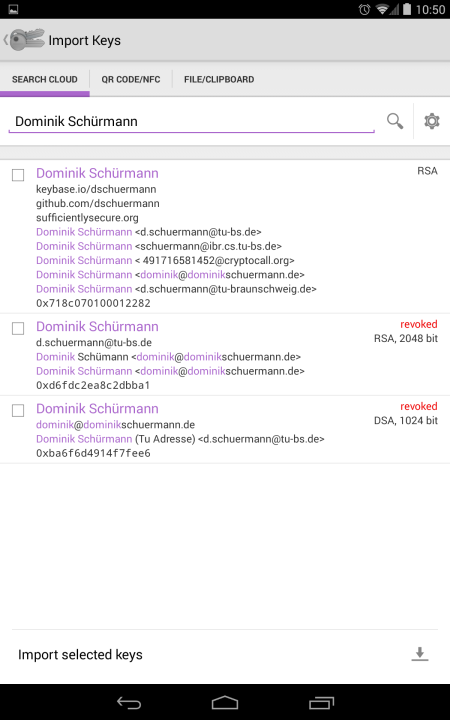
We found three keys. Two are revoked so let’s ignore them. The first listing is kind of interesting. It tells you that there’s a key for Dominik; its “fingerprint” (the closest thing keys have to a name) is “718c070100012282”. The result listing still needs some work, what with the random purple and repeated data and mysterious “0x”, but we’ll get there.
Our cloud search turned up quite a bit about that key. First, whoever controls it claims that it’s associated with a bunch of emails that look like they belong to Dominik. Second, there are claims that this key belongs to the same person who’s known as dschuermann at GitHub, and who controls the domain sufficientlysecure.org.
All this is useful when you’re deciding whether or not to believe that key is really Dominik’s. If you got it by email from one of those addresses and you’re pretty sure your email is secure, that’s good evidence. If you’re convinced that the guy you want to talk to is github.com/dschuermann, that’s useful too — but wait! Should you believe what your mobile is telling you about GitHub and so on? You don’t have to! You can check the evidence and verify the claim yourself. Which is important, but a subject for another post.
So what? · You’d be forgiven for thinking “So, you can search for keys on the Internet just like you can search for anything. What’s the big deal here?” ¶
The notion of a key server is not new — the OpenPGP keyserver software was built in the 90s — but the existing setup is hard to find, hard to talk to and, definitely not suitable for use by civilians, or really for anyone who doesn’t understand the finer points of OpenPGP as in RFC 4880.
So a modern type-and-tap interface to searching is kind of new. (I should emphasize that OpenKeychain’s nice search GUI was built by Dominik and his posse, I just made it a little shinier and richer.)
But wait, there’s more! · It turns out that when you do that search in OpenKeychain, it does a parallel search of both the old OpenPGP keyservers and Keybase.io. If you look at that search result for Dominik, the email addresses came from the keyservers and the github/sufficientlysecure.org evidence from Keybase. I’m pretty interested in Keybase, have written about it here and here. The evidence it offers, about Twitter and Github and Reddit and domains and so on, is useful and what’s best is that you don’t have to trust it to use it. ¶
Having said that, I still have a major to-do: Make that Keybase evidence verifiable right there in OpenKeychain.
And more coming! · Whatever the details, I’m pretty convinced that this notion of online key directories, of one flavor or another, has legs. And it’s not just me; the group at Google who are working on the End-to-end browser-crypto software are also talking about Key directories. The flavor they’re thinking of isn’t really like the old keyservers nor like Keybase, but is interesting. Well, if they have an API, I’ll wire ’em into OpenKeychain too. Diversity is good! ¶
When should you search? · All this raises a question: When you’re using keys to communicate securely, how often should you do this kind of cloud search for them? My answer is: Usually. As often as possible. Sometimes keys get lost or stolen and need to be revoked. Sometimes you change employers or families or countries and sometimes that means you need to change your key setup. ¶
In the current OpenPGP world, losing your key is a major pain in the butt. But in a world where people who need keys usually go fishing for them in the cloud, changing your key shouldn’t really be a serious issue.
That is, assuming some decent cloud infrastructure that’s safe to use. Which I think we’re in the process of proving is possible.

Comment feed for ongoing:
From: KB Sriram (Sep 20 2014, at 06:55)
I was thinking that an extension to your technique might be to search for confirming fingerprints published in some "well-known" way on some of the popular social profile sites. This would allow direct checks by a client, without requiring an additional service like keybase.
The signed url-as-uid on the key claims that the key is linked to the corresponding site, while a matching fingerprint published on the site claims the link the other way. Checking that both exist would provide analogous evidence as keybase, the same person in control of the key can publish to the site.
And, the obligatory link to a small java client that does this at https://github.com/kbsriram/keypan
[link]